Introducing Predictable Security
Traditional security relies on signatures, sandboxing, and behavioural analytics. The same approaches are generally repackaged with faster processing, more volume, or better marketing: “Now with AI”. The same strategy delivers the same results: warnings, unknown zero-day vulnerabilities, and breaches. The risk mitigation solution from Computed Future is unique. An attacker’s actions within an organization’s environment are taken into account, rather than standard protection and detection methods.
As an opponent, we look at security and watch threats as they evolve into assaults. Our innovative approach to security improves current security postures. We give a complete and predicted perspective of all monitored assets’ risk.
Our system “understands” skilled attackers in terms of their end-to-end processes. Unlike existing security systems, we do not focus on detecting specific signatures or artefacts like malware executables. It also means we track occurrences that may appear innocuous at first but later become part of an assault. Tracking such patterns helps anticipate assault results.
These attacks are used to train and build our attack models. These models are then used to monitor and anticipate attacks in real time. Combining attack sequence training and model extraction helps us to identify new threats.

Prevention is always better than the cure
Legislation is increasingly moving towards liability from companies that allows data to be compromised. Furthermore, there are also enforced mandatory notifications to users if their data has been compromised in a breach, rapidly eroding trust and compromising any future business.
There are compliance implications for security now. Crossing your fingers is not a viable strategy, and cyber insurance won’t cover incidents that can be attributed to neglect.
NovoFinity leverages a new approach to security technology – Predictable Security.
A fundamental shift in how cybersecurity challenges are solved, moving from simple signatures and behaviour analytics, to something new. Something that provides a comprehensive and predictive real time view of the risk of all monitored
digital assets.
Competitive analysis
How it works
Our product is deployed into your environment with minimal effort using an
automated modelling and deployment process.
Raw events are fed from origins at risk via sensors to the inference sub-system.
Progress of attacks/predictions are forwarded to your security stack via any syslog protocol compliant server or by your SIEM subscribing to the AMQP compliant
message bus
How we help prevent breaches
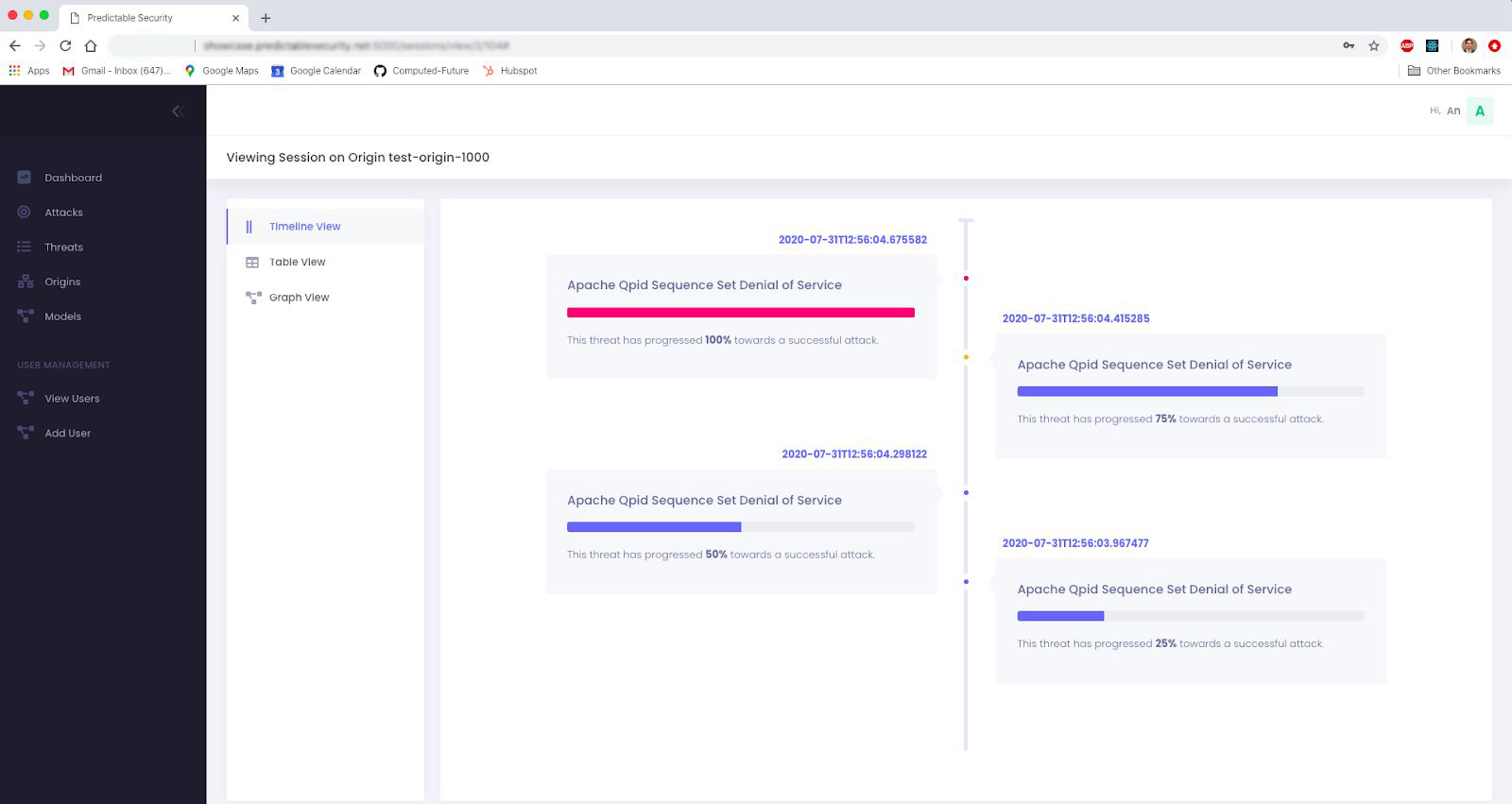
We track attack progress within your environment in real time. Based on the threat risk threshold set by your security team, we alert your team to take action on monitored resources before the attack completes. Alert fatigue and false positives are avoided through providing your security team with the ability to dive into the details of these attacks. Our glass box approach to how we monitor attacks provides your security program with unprecedented visibility. By helping your security to focus on the most relevant risks, avoid alert fatigue, and have greater visibility into attacks, we reduce your chances of a breach.
How we help in response to an attack
In contrast to existing security tools, we do not provide an alert on a specific event (network or executable on a host) only. We provide all the steps that happened on a monitored resource to bring an attack to a certain level of completion.
We provide your security team a view of all current attacks in progress (threats) in order of progress to completion. This gives an unprecedented view of risk across all monitored assets that helps the security team to focus on the most important areas of their infrastructure.
How we help in forensics
When an attack progresses to completion our technology can be used to back-track every step of such an attack. We also have metadata (such as the
operation system or source address) that sensors automatically detect or a user can configure per monitored asset (such as system names) that are associated with every detected step. Again, most steps would be considered benign by existing security tools so this ability to follow in the footsteps of the attacker
provides an amazing new capability for forensics teams.
Get the most from the data you have, and make sure it stays secure. NovoFinity ensures that you’re able to operate optimally and that you are bulletproof.